2024 ZJUCTF WriteUp
本次校赛题目质量不错,难度设置比较合适,属于是看到感觉可以试一试的程度。其中*A口算很有趣!强烈推荐!!!
MISC
小A口算
该题目会随机生成20以内的数字比较,可以构造脚本在1分钟内刷够足够分数,从而获取flag
exp
1 | from pwn import * |
成功获取flag: ZJUCTF{WoW_K1n6_0F_5h0-g4Ku-s31_4r1thm3t1c}
PWN
cake_bot
保护全开,libc版本2.34
其中保存了两个列表(或者说一个结构体列表),列表长度限制为16
cake_list: 保存malloc的cake地址cake_size_list: 保存cake的size
其中定义了Add,Show, Delete函数
- Add函数:申请新的cake,可以选择存放在列表的index,申请前检查index是否超过16,或者申请size是否不为0;然后定义cakesize,malloc对应大小的cake,然后读取对应大小的输入。
- Show函数:检查对应index的cake内容;
- Delete函数:释放对应的index的cake,这里没有将cake_list对应index堆地址置0,而且将size置0,因此可以delete后add该index。之后就可以泄露libc等内容。
思路:通过unsortedbin attack泄漏libc地址,也可以通过tcachebin泄露heap地址,还可以通过house of botcake获取栈environ地址。接下来就是通过house of botcake构造rop写入栈返回地址了
exp:
1 | from pwn import * |
获取到flag: ZJUCTF{C4ke_8ot?_8otC4ke!}
easy rop
存在栈溢出,通过泄漏libc和程序基址后获取shell。中间返回到main函数时需要考虑栈平衡,不过由于payload长度不够,所以最后将返回地址改为start函数,得解。
exp
1 | from pwn import * |
得到flag: ZJUCTF{@n_1a$y_R0p_cHalL_1N_x64|A7hdJk5wN7}
大 A 口算
首先通过已知种子为2010年的同一时间,可以预测出所有题目。
漏洞点
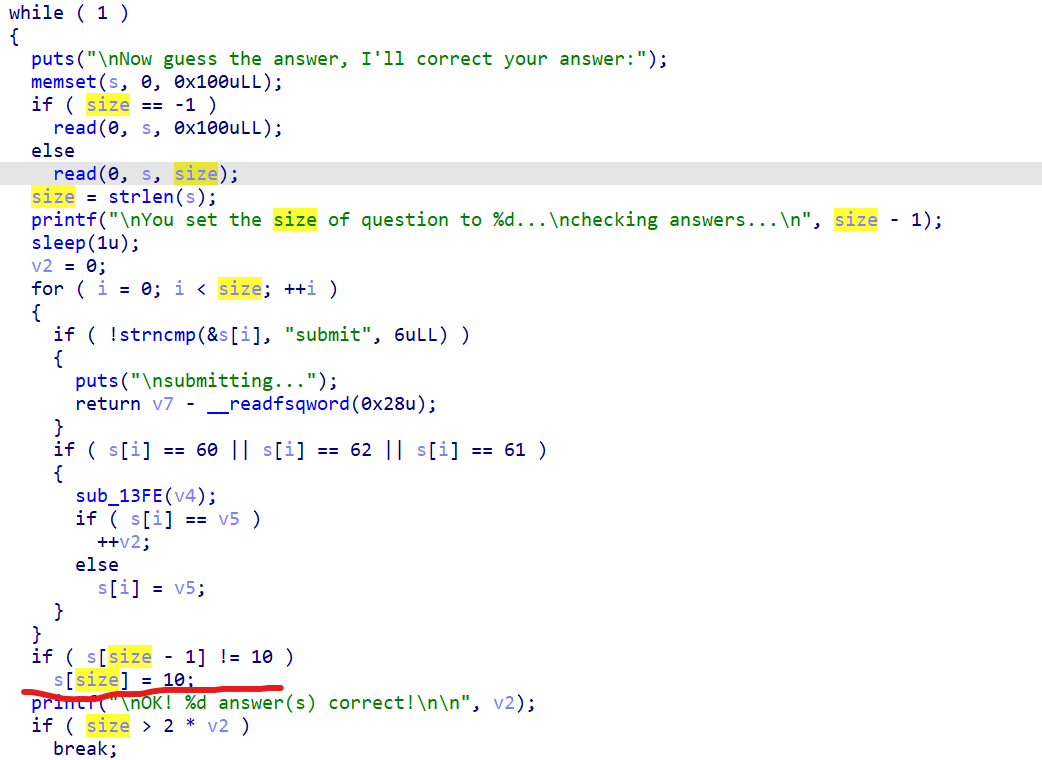
通过每次写满s变量,可以每次增加1字节,从而达到泄漏canary,partial write跳转到打印flag的函数即可。
exp
1 | from pwn import * |
得到flag: ZJUCTF{3veRY_7h1n9_1s_UNdEr_Y0uR_c0n7r0l!!}
simple echo
checksec查看保护机制:
1 | [*] '/home/brownie/ctf/matches/2024 ZJUCTF/pwn/simple-echo-attachment/app' |
ida查看,发现存在格式化字符串漏洞和栈溢出漏洞
- 首先可以通过格式化字符串漏洞获取libc基址
- 然后通过格式化字符串漏洞将rop链写入返回地址
exp
1 | from pwn import * |
得到flag: ZJUCTF{f0rMAt_5TR1Ng_bU9_iS_O1D_8uT_c001|0335}
sandbox
禁用了execve系统调用,并且不允许syscall(\x0f\x05)字节出现,同时还没有给出flag的文件名。
- 通过先传入
\x0f\x03,然后将其与\x06异或即可得到syscall。 - 通过
getdents64系统调用获取到目标flag文件名 - 通过
orw获取flag内容
exp
1 | from pwn import * |
得到flag内容:ZJUCTF{M45ter_of_O_R_W}
REVERSE
rev beginner 1
基础逆向题:
exp
1 | from pwn import * |
得到flag: ZJUCTF{rev_is_fun_right?}
rev beginner 2
基础逆向题,通过模拟das指令进行逐字符爆破,得到flag
exp
1 | from pwn import * |
得到flag:ZJUCTF{welc0me-2-reverse!}
中 A 口算
其种子为2010年同一时间,因此可以预测所有的题目。
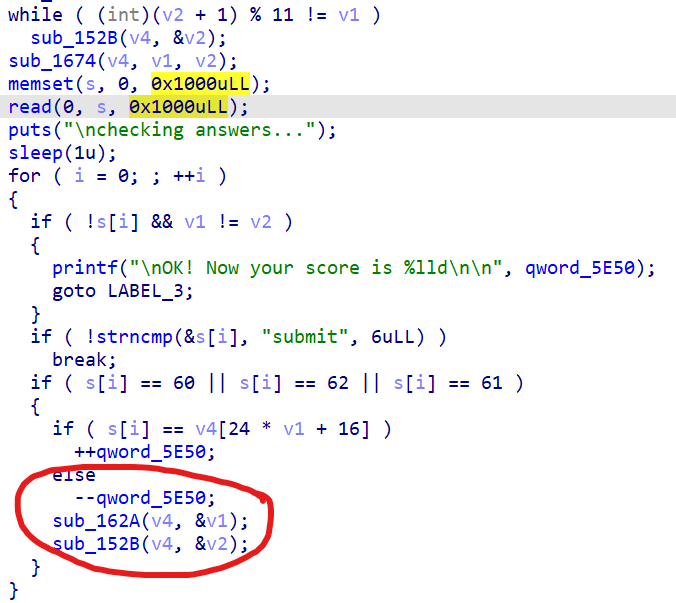
如图,只要存在answer,就会一直生成题目,因此可以一次输入足够长(0x1000长度)的答案,可以快速得分
exp
1 | from pwn import * |
flag: ZJUCTF{5aK1-CHan's_k0k0r0_ls_5m4sh3d_oTATo}
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)